Gavin Ashton was an IT security guy working at Maersk at the time of it was hit hard by the NotPetya ransomware. Now he’s written an article about his experiences, and shares advice for others.
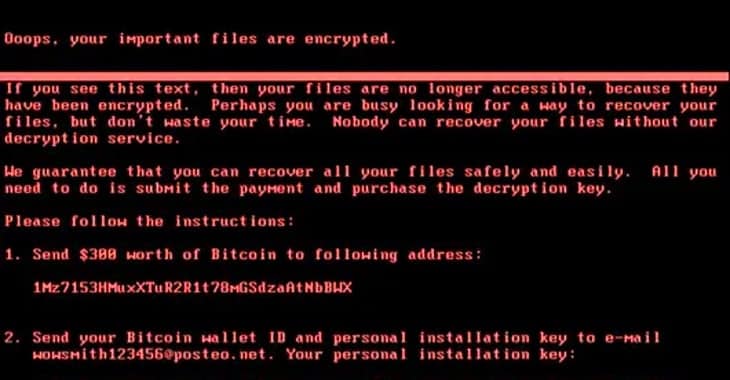
The shipping conglomerate Maersk, hit by the NotPetya ransomware in June 2017, estimated that it cost them as much as $300 million in lost revenue.
Gavin Ashton was an IT security guy working at Maersk at the time of the attack. He’s now written an in-depth article about what happened.
I want to help protect other folks from making these same mistakes, because there’s a lot of what seems to be defeatist wisdom out there; Yes, it is inevitable that you will be attacked. It is inevitable that one day, one will get through. And obviously, you should have a solid contingency plan in place in case of the worst. But that’s not to say you don’t attempt to put up a damn good fight to stop these attacks in the first case. Just because you know the bad actors are coming, doesn’t mean you leave your front door open and make them a cup of tea when they walk in. You could just lock the door.
Staying with the home analogy; Yes, there’s security cameras and wizard cloud-connected ‘Internet of Things’ (IoT) devices and all kinds of expensive measures and widgets, but a lot of organisations fail simply on the basics. Lock the damn door.
It’s a good read, and strongly recommended if you’re responsible for securing your enterprise from malware attack.
And make sure to check out this “Smashing Security” podcast we recorded back in June 2017, at the time of the outbreak:
Source : The inside story of the Maersk NotPetya ransomware attack, from someone who was there
