Belonging to the Crysis/Dharma malware family and discovered by Jakub Kroustek, Bot is malicious software categorized as ransomware. Bot operates by encrypting data and demanding ransom payments for decryption (i.e. payment for decryption software/tools and keys).
During the encryption process, all files are renamed with a unique ID number generated individually for each victim, Bot developer’s email address, and the « .bot » extension. Therefore, « 1.jpg might be renamed to a filename such as « 1.jpg.id-1E857D00.[nmode@tutanota.com].bot« , and so on for all files.
After this process is complete, a text file (« RETURN FILES.txt) is created on the desktop and a pop-window is displayed. Updated variants of this ransomware use « .[catchbtc797@protonmail.com].bot« , « .[admin@sectex.net].bot » and « .[grdoks@tutanota.com].bot » extensions for encrypted files.
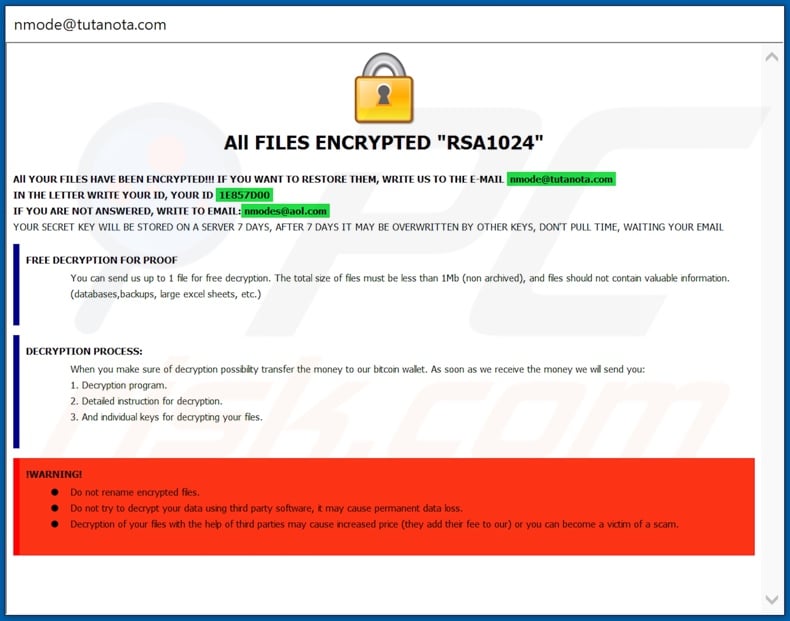
The text file informs affected users that their data has been encrypted. If they wish to retrieve it, they must contact the cyber criminals behind Bot ransomware. The pop-up window contains a detailed ransom message. It states that victims’ data has been encrypted using the RSA encryption algorithm, and to restore it, they must send an email using the address provided.
Should there be no response, an alternative email address is provided. The email must contain the victim’s unique ID number. The developers of Bot warn that decryption keys will only be stored on their servers for seven days and, therefore, victims must not delay in contacting them.
As ‘proof’ of their ability to recover the data, the criminals offer to decrypt one file free of charge. The file must be no larger than 1 MB (non-archived) and contain no ‘important information’ such as backups, databases, large excel sheets, etc. The size of the ransom is not stated, however, it must be paid in the Bitcoin cryptocurrency.
Once the transfer is complete, victims are promised detailed instructions about how to decrypt their data, a decryption program, and necessary keys. The message lists further warnings: users are instructed not to rename encrypted files or attempt manual decryption, otherwise they risk permanent data damage.
There are no free tools capable of breaking Bot’s encryption. Only the software used to encrypt files is capable of decryption. Nevertheless, you are strongly advised against meeting the ransom demands. Despite paying, users often receive none of the promised tools and their data remains encrypted and useless.
The only solution is to restore files from a backup, provided one was made before the ransomware infection and stored separately.
Screenshot of a message encouraging users to pay a ransom to decrypt their compromised data:
Typically, ransomware-type programs share certain similarities. For example, Uta, MedusaLocker, HORSELIKER, Bora are similar to Bot. Malicious software of this kind encrypts data and demands ransom payments for recovery. They differ by cryptographic algorithm used (symmetric or asymmetric) and the size of ransom.
The latter usually ranges between three-digit and four-digit sums (in USD). Cyber criminals prefer digital currencies (e.g. cryptocurrencies, pre-paid vouchers, etc.), as these transactions are difficult/impossible to trace. Manual decryption (without the involvement of the developers) is impossible unless the ransomware is still in development and/or has bugs/flaws.
To ensure data safety, keep backups on remote servers and/or unplugged storage devices. As these are liable to damage, store several backup copies in different locations.
How did ransomware infect my computer?
Malicious software/content is commonly proliferated through spam campaigns, trojans, untrustworthy download channels, fake software updaters, and « cracking » tools. Massive scale spam campaigns are used to send out deceptive emails containing infectious attachments.
These messages are usually marked as « important », « official », or otherwise highlighted as urgent mail. The attachments can be in various file formats (e.g. archive and executable files, PDF and Microsoft Office documents, JavaScript, etc.). When opened, they download/install malware.
Trojans are malicious programs designed to cause chain infections. Untrustworthy download sources include P2P sharing networks (BitTorrent, eMule, Gnutella, etc.), unofficial and free file-hosting sites, third party downloaders and similar. These can offer deceptive and/or bundled content.
Fake updaters exploit weaknesses in outdated programs and/or install malware rather than the promised updates. Software « cracking » tools can download/install malicious programs, rather than activate licensed products.
