Artificial intelligence (AI) adoption is on the rise. According to a recent McKinsey survey, 55 per cent of companies use artificial intelligence in at least one function, and 27 per cent attribute at...
A new method automatically describes, in natural language, what the individual components of a neural network do. Neural networks are sometimes called black boxes because, despite the fact that they c...
Over the past decade a niche of fintech wealth management firms including Wealthfront, Personal Capital and Betterment tackled one of the biggest disruptive challenges: financial services. Wealthfront...
Cybersecurity teams are eager to deploy AI-powered tools and are driven by factors including persistent hiring challenges. Vendors are eager to sell their AI-powered tools either to differentiate thei...
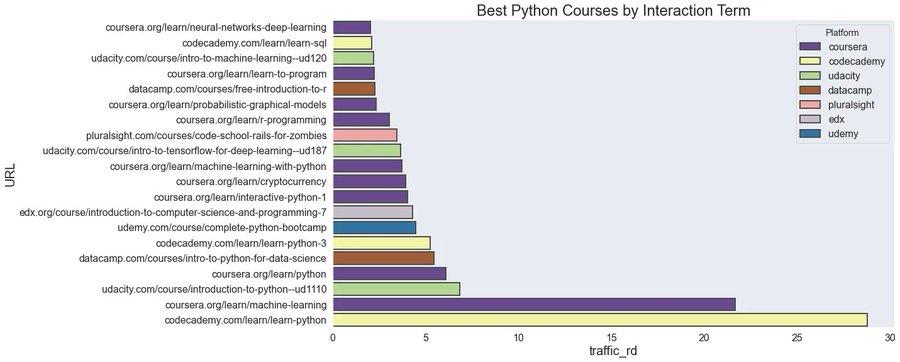
What does the data reveal if we ask: « What are the 10 Best Python Courses? ». Collecting almost all of the courses from top platforms shows there are plenty to choose from, with over 3000 offerings. ...
Machine learning tools are used in a variety of fields, from sales to medicine. But getting tech into the workplace is just one step — these tools are only successful if they’re integrated into workfl...
While business leaders grapple with the problem of cybercrime, they may be overlooking the giant cybercrime wave that quantum computing will bring. Quantum supremacy is the inflection point at which q...
Tesla’s Director of Artificial Intelligence, Andrej Karpathy, says that he believes ‘Tesla Bot’ is “on track to become the most powerful AI development platform.” Since Tesla AI Day last year, CEO Elo...
Precious metal investors have faced a grueling year as gold prices contracted after two years of gains. In recent days, however, gold and silver prices reached their highest levels since the sharp sel...
Russian President Vladimir Putin has called for consensus between his country’s government and the central bank following the latter’s recent call for an outright ban on crypto. Speaking i...
The debate over whether AI will replace humans in the workforce often boils down to a handy, twofold explanation: AI will replace humans for most repetitive and manual labor tasks, while humans will e...
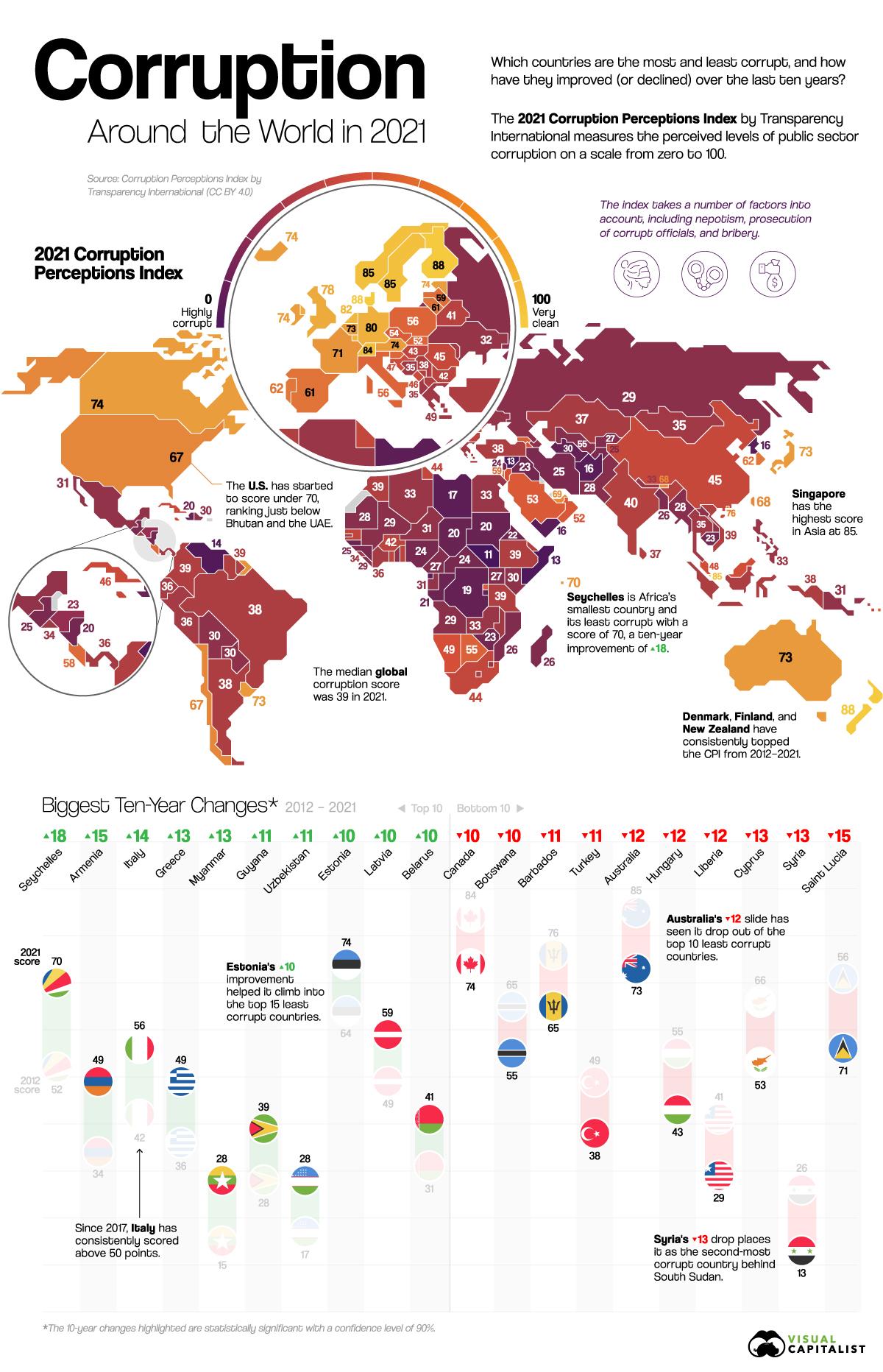
How bad is public sector corruption around the world, and how do different countries compare? No matter your system of government, the public sector plays a vital role in establishing your economic mo...
An artificial intelligence system is capable of spotting whether someone will have a heart attack within the next year — through a routine eye scan. A team from the University of Leeds believes this A...
Fintech companies have established themselves as viable competitors in the financial-services business, but now they face a new challenge: Some mainstream banks have started to offer fintech-inspired ...
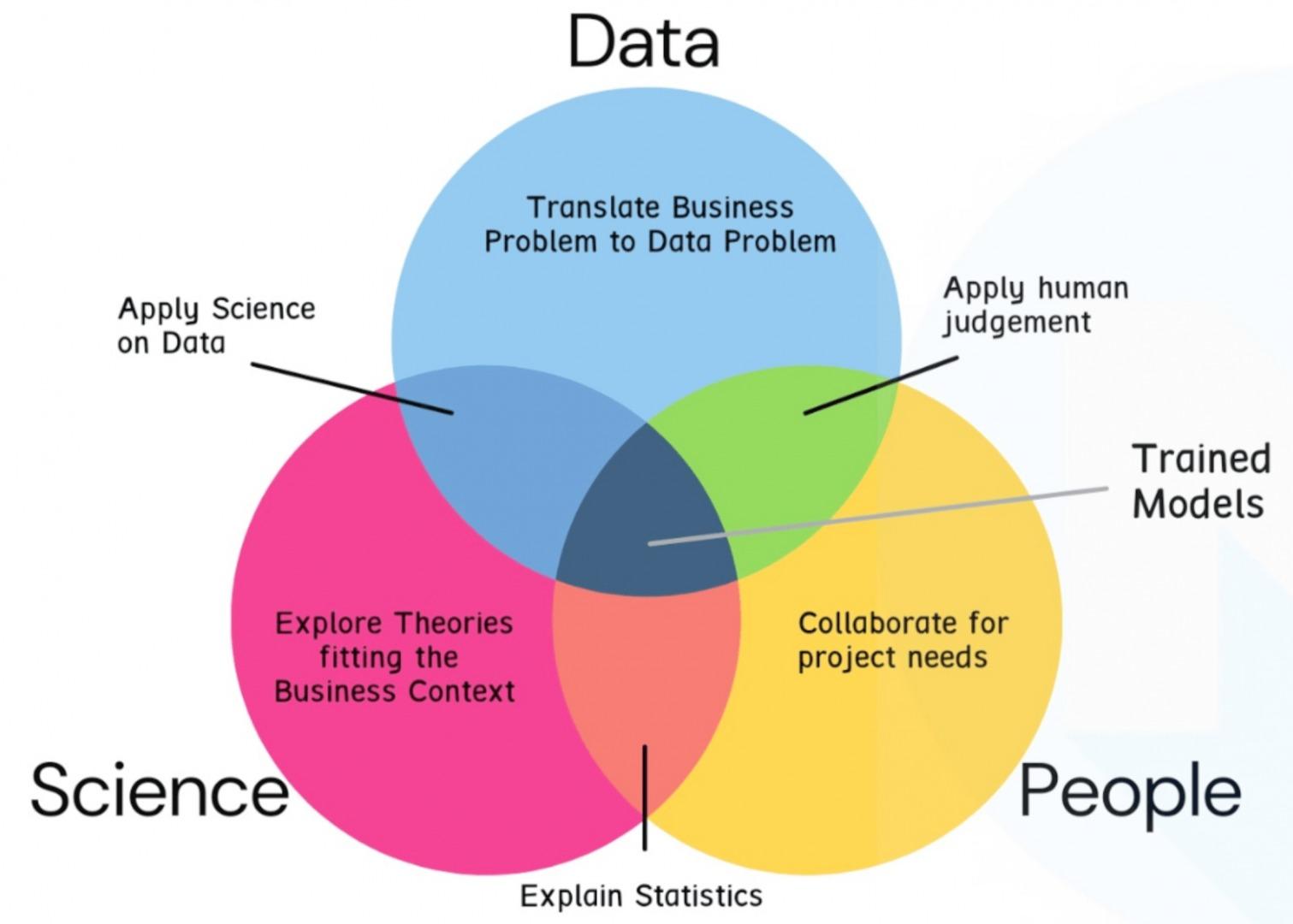
Organisations are revamping their data science and engineering strategies to gain the necessary skills to deploy artificial intelligence (AI) and machine learning (ML) systems. Companies are now hirin...