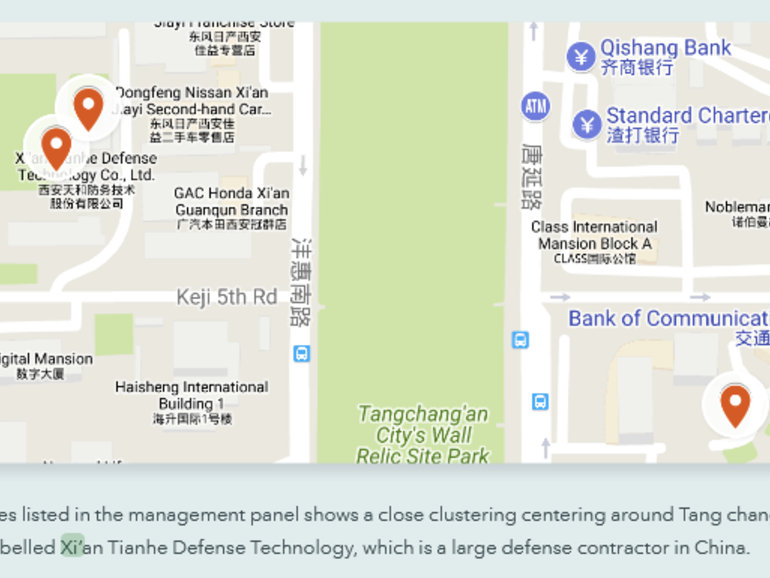
Lookout said it linked APT15 malware to Xi’an Tianhe Defense Technology, a Chinese defense contractor. In a report published today, cyber-security firm Lookout said it found evidence connecting ...
China’s Foreign Ministry has escalated its attacks on Australia, accusing the Federal Government of conducting espionage in China and calling tabloid claims of Australian spying the « tip of the...
Do you think you have found a vulnerability in the Sony PlayStation 4 or the PlayStation Network? If so, you could be heading towards a sizeable sum of money. That’s because Sony announced details of ...
) on LinkedIn to break into the networks of military contractors in Europe, cybersecurity researchers said on Wednesday. The cyber spies were able to compromise the systems of at least two defence and...
Facebook a enfin coincé un pédophile récidiviste qui se cachait sur sa plateforme. Mais pour y parvenir elle a dû participer au développement d’un outil de hacking pour un logiciel tiers, qu&rsq...
Cryptomining hacks aren’t new by any stretch, but a string of recent incidents is raising eyebrows. ZDNet reports that culprits infected multiple European supercomputers with Monero mining malware in ...
The Senate rejected an amendment to the Foreign Intelligence Surveillance Act that would have prevented the government from accessing Americans’ web browsing data without a warrant on Wednesday....
Cisco Systems and Palo Alto Networks have fixed similar high-risk authentication bypass vulnerabilities in their network security devices that were caused by an oversight in the implementation of the ...
Un investisseur de crypto-monnaie a accusé un pirate informatique et son équipe de pirates informatiques mineurs d’avoir volé 24 millions de dollars en crypto-monnaie via une attaque par échange...
One tool that bad guys use to go after your web servers is a web shell. A web shell is a malicious script that masquerades as a legitimate file and provides a backdoor into your server. Recent guidanc...
In its latest research, cybersecurity solutions provider Trend Micro revealed how advanced hackers could leverage unusual and new attack vectors to disrupt smart manufacturing units. For the research,...
Les escrocs s’attaquent aux utilisateurs des médias sociaux pour les offres à l’approche de la fête des pères et d’autres occasions de cadeaux, attirant le public avec des «offres ex...
GoDaddy a récemment informé une partie de ses 19 millions de clients qu’un pirate avait pu accéder à leurs comptes SSH, et qu’il était probable qu’il ait pu visualiser et exfiltrer d...
“This is the most extensive operation we have ever reported by a Chinese APT group,” the cyber researchers at Check Point told me, warning just how “targeted and sophisticated” this five-year campaign...
Europol a arrêté cinq membres du groupe de hackers Infinity Black qui vendaient des identifiants d’utilisateurs volés et des outils de piratage. Europol a annoncé un autre succès dans la lutte c...