On 30 July 2021, the Federal Court of Australia decided that AI systems can be inventors. In a word-first determination of Thaler v Commissioner of Patents,{[2021] FCA 879, (‘Thaler’)}, the Honourable...
A wave of sanctions hitting Russia highlights the complex web of connections that make up contemporary global society – and its ultimate fragility. Vladimir Putin’s Russia is facing a wave of truly un...
Artificial intelligence (AI) is becoming the dominant trend in data ecosystems around the world, and by all counts, it will accelerate as the decade unfolds. The more the data community learns about A...
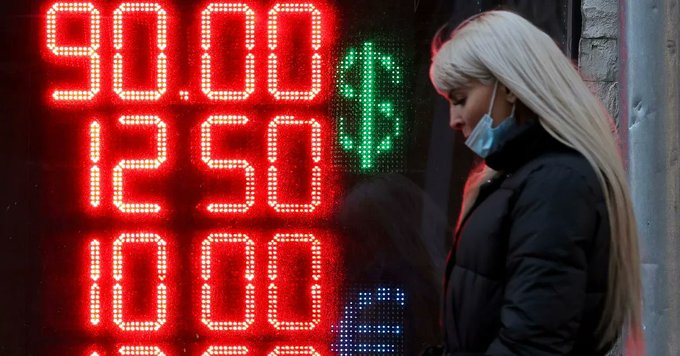
KEY POINTS Washington takes aim at Russia’s access to digital cash as the U.S. and its allies levy heavy punitive measures against Moscow. The concern is that the Kremlin, as well as other ancillary a...
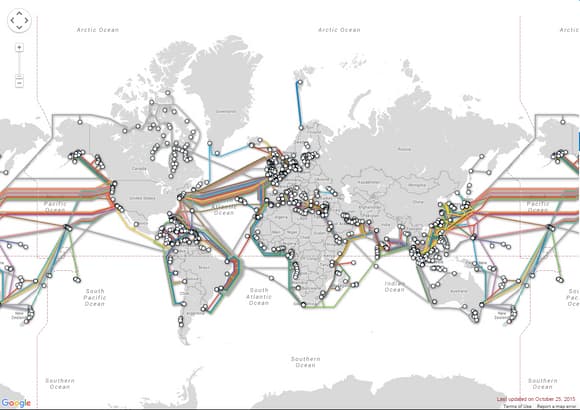
Une menace plane sur les câbles sous-marins qui relient les continents à Internet. Une coupure provoquerait un blackout. Ce scenario cauchemardesque est envisagé par les forces armées. Après 7 jours d...
What causes someone to change banks? According to PYMNTS research, consumers who are most likely to switch their primary financial institution (FI) typically cite several areas of innovation. Thirty-f...
A novel investigation by STAT and the Massachusetts Institute of Technology found that subtle shifts in data fed into popular health care algorithms — used to warn caregivers of impending medical cris...
Responsible practices using tested processes must be the focus when creating new technology. Technology has always been a double-edged sword. While it’s been a major force for progress, it has also be...
Recently, with the push in the AI sector, machine learning and deep learning have been on the rise and the early adopters of these technologies are starting to see their results. More and more busines...
The Internet of the future might be something completely different from what we know currently. But this change will be for the better good or worse. Experts from Copenhagen Institute for Future Studi...
Cryptocurrency hacks usually make the news. So do arrests of alleged perpetrators. The recent seizure of around $3.6 billion worth of bitcoin along with the highly publicized arrest of two individuals...
In late 2019, we published “7 Classic Books To Deepen Your Understanding Of Artificial Intelligence.” It’s time to run it back. Here are 7 more thought-provoking books that explore the technology, bus...
The world is still a long way off from human-like AI (artificial intelligence), according to experts at a Feb. 24 event by Facebook parent Meta. “When you train a system with a data set, the data is c...
If you think that hiring data scientists or deploying machine learning algorithms makes your organization an AI-driven company, you may be completely wrong. Indeed, you may be anything but AI-driven. ...
The Unchain fund has raised $1.8 million and plans to launch a DAO this week, even as team members live with sirens, explosions and artillery barrage following the Russian invasion. After Russia invad...