Academic researchers are developing projects to apply AI to detect and stop cyberattacks and keep critical infrastructure secure, thanks to grants from C3.ai Digital Transformation Institute. 7 Ways t...
In the example directly above, the real-life video on the right (woman in red dress) is used to ‘puppet’ the captured identity (man in blue shirt) on the left via RigNeRF, which (the authors claim) is...
Security researchers have warned of « increasing and unsustainable stress levels » in the cybersecurity workforce resulting from persistent ransomware threats and looming, large-scale attacks, which a...
Actor Val Kilmer lost his voice to throat cancer, yet in the new “Top Gun” movie, he does speak a line, thanks to an artificial intelligence program that recreated his voice. That is a good use of aud...
Lack of in-house, on-demand cybersecurity skills and implementation expertise have been identified as crucial barriers to raising advanced cyber defense infrastructure in key Asia Pacific. 89% of orga...
Cybercrime continues to grow at an astounding and devastating rate; more than 93% of organizations in the healthcare field alone experienced a data breach in the past few years (Sobers, 2021). While m...
45% of cybersecurity pros are considering quitting the industry due to stress Deep Instinct released the third edition of its annual Voice of SecOps Report, focused on the increasing and unsustainable...
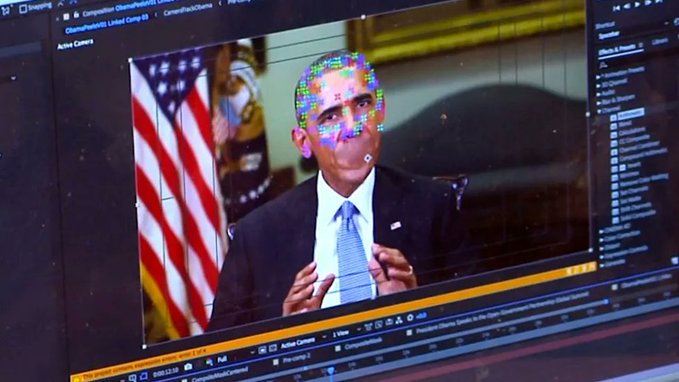
What’s this about: AI-generated media is one tool in the AI arsenal being deployed by governments and independent actors all across the globe. This new and effective tool is often used to target polit...
Artificial intelligence has advanced greatly in the past decade. On my phone, I’m reading Apple and Google news that is well-tailored to me, thanks to AI recommendation models. Self-driving cars...
Opinion When Generative Adversarial Networks (GANs) first demonstrated their capability to reproduce stunningly realistic 3D faces, the advent triggered a gold rush for the unmined potential of GANs t...
When law professor Douglas Branson published the book The Future of Tech is Female in 2018, he must have imagined that the global tech industry would soon be led by women. Four years later, that futur...
In the video record of the Ukraine war, a clumsy attempt to “deepfake” Ukrainian President Volodymyr Zelensky coexists alongside critical on-the-ground video evidence of abuses, pervasive misinformati...
Deep fakes are a type of artificial intelligence that can be used to recreate the likeness of a real person. A deep fake can indeed duplicate a face, but modern iPhones cannot be unlocked by a picture...
Google has banned the training of AI systems that can be used to generate deepfakes on its Google Colaboratory platform. The updated terms of use, spotted over the weekend by Unite.ai and BleepingComp...
Le metaverse et la crypto monnaie semblent être des concepts qui vont de pair. Tous deux font partie intégrante du « web3 », la troisième génération d’internet, après web1 (le world-wide-web), et web2...