When a group of German hackers breached a Tesla, they weren’t out to remotely seize control of the car. They weren’t trying to access the owner’s WiFi passwords, nor did they want a way to steal credi...
Wondering why you’re seeing videos of a national news anchor promoting a cannabis company on YouTube? Or why tech billionaire Elon Musk is being featured in an ad promoting an investment opportu...
Too often, investments in technology fail to achieve promised results. Why is that? And what can companies do to change it? When tech projects go bust, executives too often focus on the symptoms, not ...
Identity and access management solutions provider Okta warns that multiple customers based in the United States have been targeted in sophisticated attacks involving social engineering. The company sa...
La frénésie des investissements dans l’IA générative est-elle ancrée dans une réalité économique ? Selon plusieurs analystes interrogés par le magazine Institutional Investor, le domaine attire ...
La CNIL prévoit de publier début 2024 une recommandation sur la sécurité des « traitements critiques ». L’autorité met en ligne le projet de texte et lance une consultation publique. Certains se...
Ransomware Definition Ransomware is a type of malicious software cybercriminals use to block you from accessing your own data. The digital extortionists encrypt the files on your system and add extens...
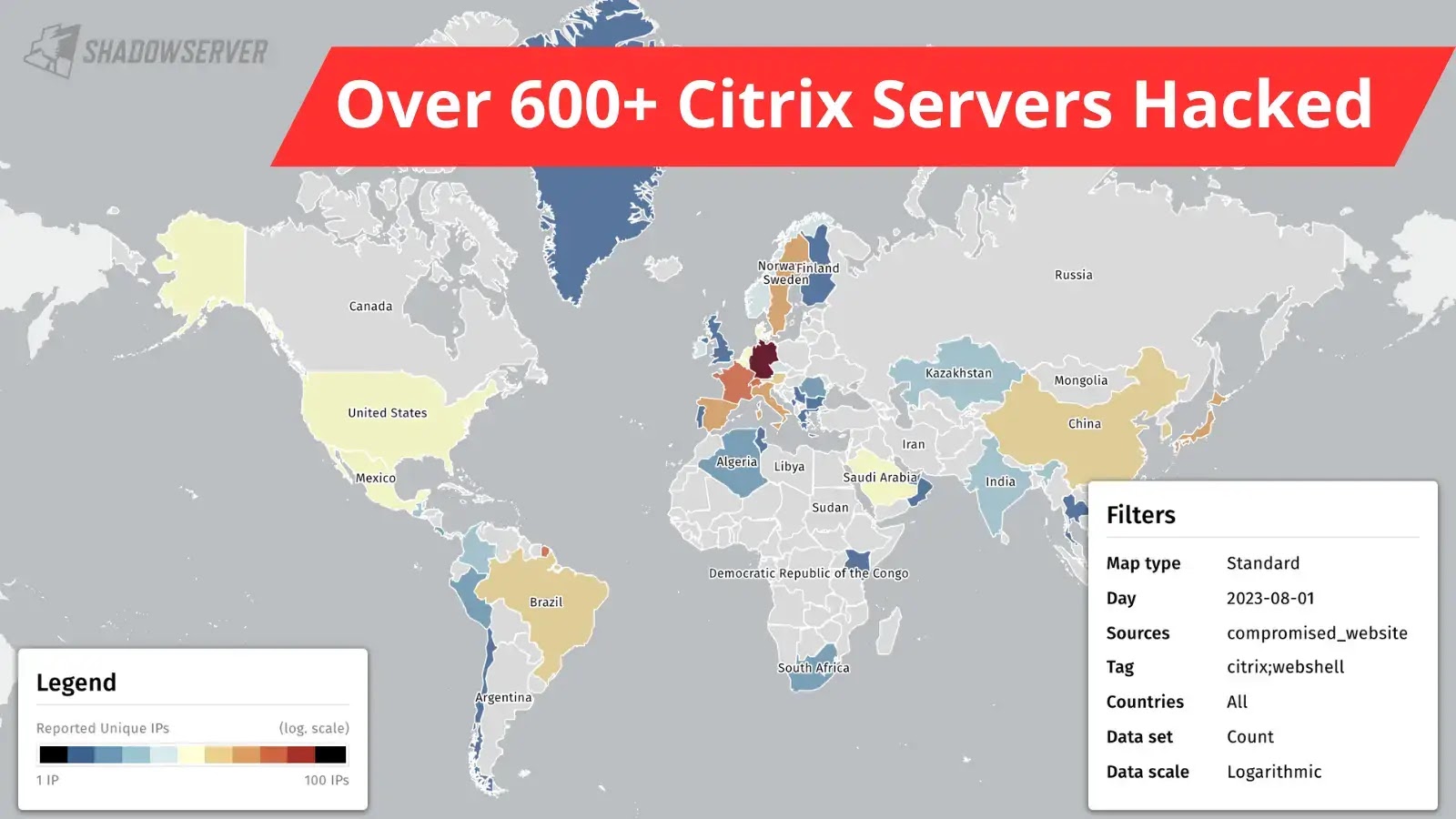
A critical remote code execution (RCE) vulnerability identified as CVE-2023-3519 has been the subject of several attacks, which have already compromised and backdoored hundreds of Citrix Netscaler ADC...
Le consultant ou la consultante en cybersécurité accompagne les entreprises, administrations et start-ups pour sécuriser leurs systèmes et réseaux informatiques. Description métier Spécialiste et gara...
When OpenAI launched the generative AI chatbot ChatGPT for public use on Nov. 30, the S&P 500 was worth $5 trillion less than now, tech spending was deep in a post-pandemic hangover, and the econo...
Plus de 500 établissements de santé ont réalisé « au moins un premier exercice de gestion de crise cyber », se félicite l’Agence du numérique en santé, qui avait contribué à élaborer des « kits ...
Advances in generative artificial intelligence could supercharge the propaganda playbook, experts warn Abanal dystopia where manipulative content is so cheap to make and so easy to produce on a massiv...
Scam calls using AI to mimic voices of people you might know are being used to exploit unsuspecting members of the public. These calls use what’s known as generative AI, which refers to systems capabl...
When it comes to cybersecurity, organizations are constantly looking for new ways to improve their defenses. A promising area of research is combining cybersecurity with machine learning (ML). This wa...
Powerful AI tools are changing the world of cybersecurity. But while businesses should embrace these new innovations, it is critical they do so responsibly From privacy breaches to ransomware attacks,...