Yesterday, beginning at 18:24 UTC, someone or something exploited a security vulnerability on Wormhole, a tool that allows users to swap assets between Ethereum and a number of blockchains, resulting ...
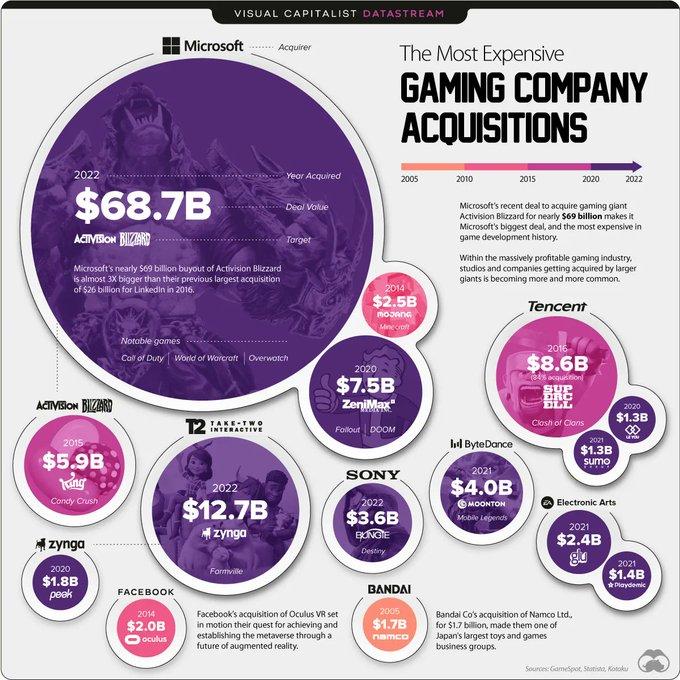
Not even a week after Take-Two Interactive acquired mobile game developer Zynga for $12.7 billion, Microsoft claimed the title for the most expensive gaming acquisition in history. The tech giant will...
The season 2 finale of The Mandalorian was an emotional roller coaster for a lot of fans (including me), but there was one big reveal that’ll most likely have fans debating until the hit show re...
We’ve seen technological advances before. But never have we seen the convergence of so many new technologies changing so much so fast. This moment is challenging American intelligence agencies in thre...
Cybersecurity has undergone massive shifts technology-wise, led by data science. The extraction of security incident patterns or insights from cybersecurity data and building data-driven models on it ...
Cybersecurity issues are widely seen as the greatest risk to company growth in the next three years. There is a global shortage of suitably trained and qualified people to work in cybersecurity. Artif...
You wouldn’t expect the mention of ancient cartographers, or famous names like Vespucci, to evoke thoughts of cybersecurity. But cybersecurity truths are like cyberattackers — they pop up in unexpecte...
LIKE SEEMINGLY everyone these days, Moxie Marlinspike has created a non-fungible token (NFT). These digital chits use clever cryptography to prove, without the need for a central authenticator, that a...
I recently read a book called The Age of AI. The book was intended to provide an overview of the approaching trends for artificial intelligence (AI). The purpose of this article is not meant to provid...
What is the general public’s impression of artificial intelligence (AI)? It isn’t always easy to gauge. AI-powered voice assistants like Siri and Alexa are in our phones, our homes and even our cars, ...
Artificial intelligence (AI) adoption is on the rise. According to a recent McKinsey survey, 55 per cent of companies use artificial intelligence in at least one function, and 27 per cent attribute at...
Cybersecurity teams are eager to deploy AI-powered tools and are driven by factors including persistent hiring challenges. Vendors are eager to sell their AI-powered tools either to differentiate thei...
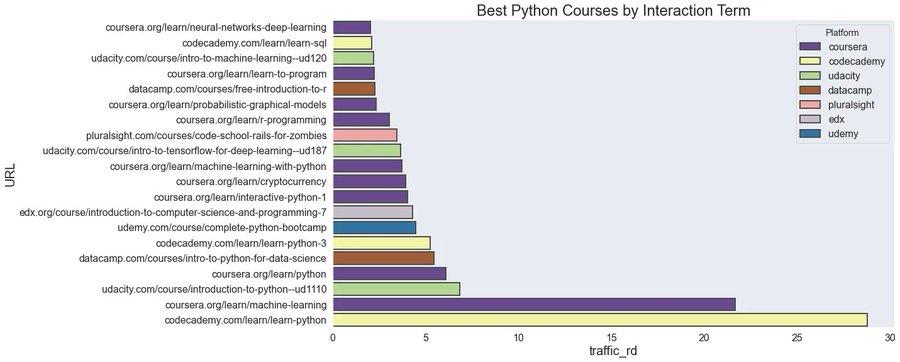
What does the data reveal if we ask: « What are the 10 Best Python Courses? ». Collecting almost all of the courses from top platforms shows there are plenty to choose from, with over 3000 offerings. ...
Machine learning tools are used in a variety of fields, from sales to medicine. But getting tech into the workplace is just one step — these tools are only successful if they’re integrated into workfl...
While business leaders grapple with the problem of cybercrime, they may be overlooking the giant cybercrime wave that quantum computing will bring. Quantum supremacy is the inflection point at which q...