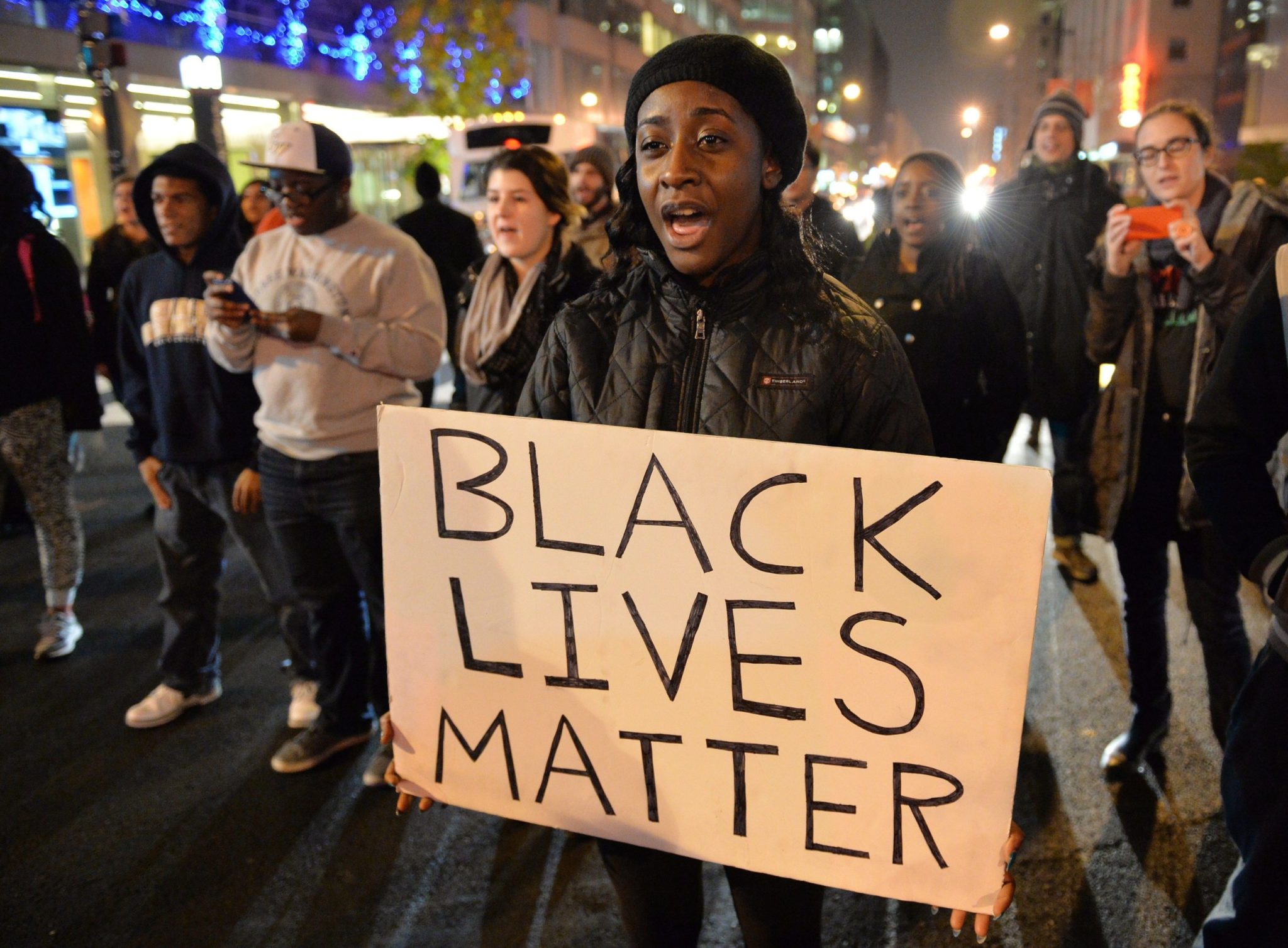Comptant parmi les secteurs les plus sensibles, le monde du transport est en pleine transformation, de plus en plus connecté et exposé à des cyberattaques potentiellement dévastatrices. Dans ce contex...
D’après Engadget ,certains utilisateurs d’Instagram ont eu la désagréable surprise de voir des posts bloqués lorsqu’ils comportaient le #blacklivesmatter, mouvement antiraciste américain. Le message d...
Apple vient de déployer une mise à jour pour corriger une faille zero day qui permettait à une application de prendre le contrôle d’un iDevice et autorisait ainsi le jailbreak de n’importe quel appare...
Internet of Things (IoT) devices offer tremendous capabilities to users. Looking around I see more and more ways, especially in a post COVID-19 world, that these devices will make our lives easier and...
The latest social media craze Mitron app has a critical vulnerability. As discovered, the bug allows an adversary to takeover TikTok Alternative Mitron App Has A Critical Vulnerability Allowing Accoun...
Read the original article: SOAR can help organizations manage their data security efficiently through automation and orchestration In physics, the rate of acceleration is known as “jerk.” A commonly u...
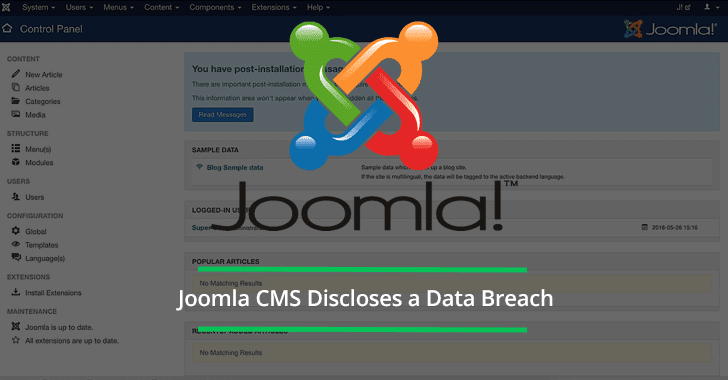
Joomla is a popular free and open-source content management system used for publishing web content. The team behind the CMS discloses the data breach last week. The incident happens after a team membe...
A wave of cyber-spying around COVID-19 medical research is once more demonstrating the perils of treating cybersecurity as a separate, walled-off realm. Driving the news: U.S. officials recently annou...
Un nouveau plugin buggué permet à des cybercriminels de prendre le contrôle et de supprimer toutes les données d’un site internet tournant avec WordPress. Pas une, mais deux failles de sécurité ...
A group of business email compromise (BEC) Nigerian scammers has been targeting U.S. unemployment systems and COVID-19 relief funds provided through the CARES Act. The threat actor, which researchers ...
The digital threat landscape is always changing. This year is an excellent (albeit extreme) example. With the help of Dimensional Research, Tripwire found out that 58% of IT security professionals wer...
Almost daily now there is news about flaws in commercial software that lead to computers getting hacked and seeded with malware. But the reality is most malicious software also has its share of securi...
3 hours ago Andy Greenberg / Wired A technique called NXNSAttack that could allow a relatively small number of computers to carry out distributed denial of service (DDoS) attacks on a massive scale, o...
Les opérateur du rançongiciel Sodinokibi continuent leur divulgation des données du cabinet d’avocat des stars GSM Law. Après avoir publié les données relatives à Lady Gaga, ils affirment qu&rsq...
Le Cloud est l’un des piliers de la transformation numérique. Pour autant, 90 % des organisations se déclarent préoccupées par la sécurité dans le Cloud. Celui-ci invite à se tourner vers de nou...