L’entreprise accusée de récupérer illégalement des données sur les utilisateurs de Facebook a refusé de se soumettre à un audit. Facebook poursuit également l’exploitant d’un site ve...
Spécialisé dans la diffusion illégale de films et séries, souvent avant même leur sortie officielle, le groupe Sparks a vu deux de ses membres arrêtés. Source : Piratage : deux membres du groupe Spark...
Et si, quand vous demandiez à Alexa de lire la météo, elle activait des caméras et envoyait un flux d’image vers l’extérieur ? [Lire la suite] Source : Des chercheurs ont infecté des sites...
Les CDO (Chief Data Officer) peuvent avoir du mal à montrer des avantages significatifs de l’exploitation des données à leur direction. Se concentrer sur la communication, la numérisation et la ...
Quel sera l’impact de la pandémie liée au Covid-19 sur les métiers IT en Europe ? Comment évolueront les compétences (…) Source : Covid-19 : Un coup d’accélérateur à la numérisation des em...
La nouvelle politique de Google Ads entrera en vigueur le 1er septembre 2020. Source : A l’approche des élections américaines, Google interdit les publicités liées à du contenu politique piraté ...
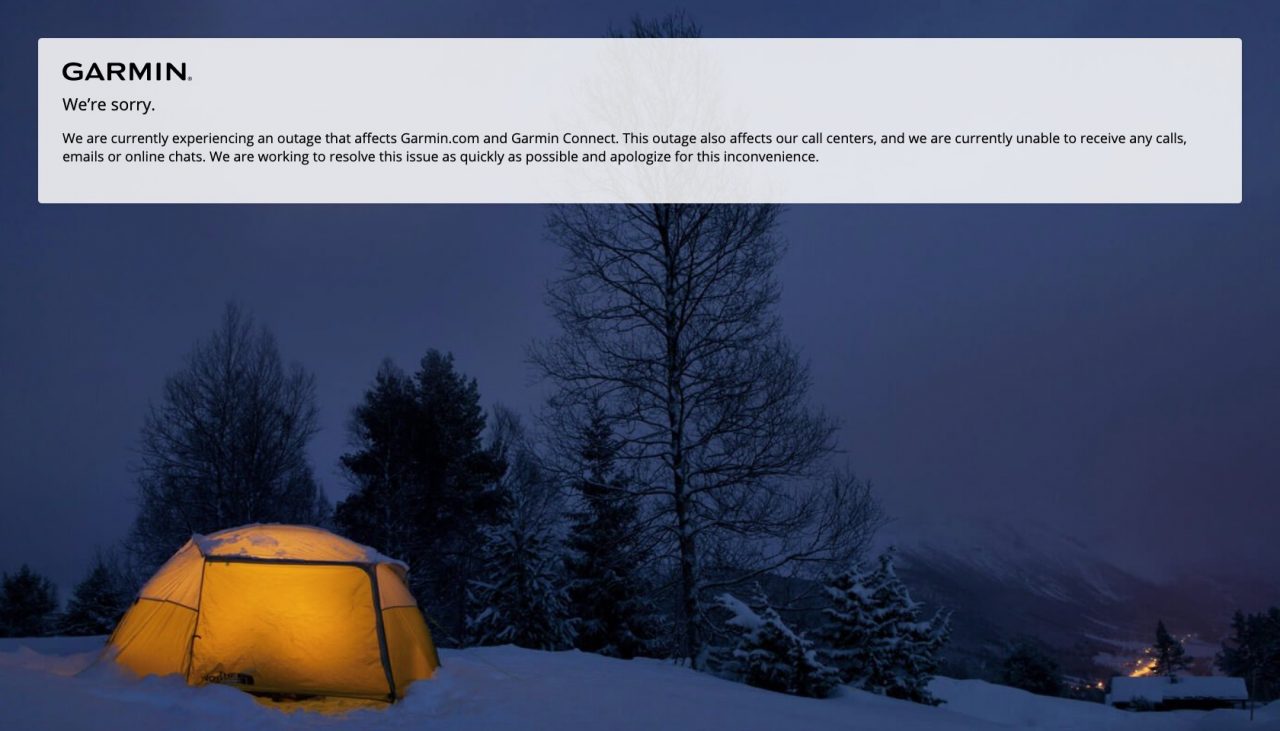
Garmin’s services, websites and customer service have all been down since Wednesday night. Garmin, maker of fitness trackers, smartwatches and GPS-related products, has reportedly suffered a wid...
Industry and academic research into a selection of self-certified electronic logging devices found those in the sample did little to nothing to follow cybersecurity best practices and were vulnerable ...
Apple Security Research Device Program As part of Apple’s commitment to security, this program is designed to help improve security for all iOS users, bring more researchers to iPhone, and improve eff...
A new cryptojacking botnet is spreading across compromised networks via multiple methods that include the EternalBlue exploit for Windows Server Message Block (SMB) communication protocol. Researchers...
The North Korean APT has been using the framework, called MATA, for a number of purposes, from spying to financial gain. The North Korean APT has been using the framework, called MATA, for a number of...
Lorien Health Services in Maryland announced that it was the victim of a ransomware incident in early June. Data was stolen and then encrypted during the incident. A family-owned nursing home for the ...
Welcome to the Network Ethical Hacking course! Hacking is a science similar to any other science. In this course I am going to show you the basics of hacking which will support you to start by yoursel...
The more we depend on smartphones, the more attractive an attack vector they become. Android and iOS and devices have become common targets for cybercriminals, as people use them for work, communicati...
How to Know If You’ve Been Hacked, and What to Do About It Facebook. Google. Netflix. Sometimes your accounts get compromised, so it’s vital to understand the threats. The average person will likely f...