You wouldn’t expect the mention of ancient cartographers, or famous names like Vespucci, to evoke thoughts of cybersecurity. But cybersecurity truths are like cyberattackers — they pop up in unexpecte...
LIKE SEEMINGLY everyone these days, Moxie Marlinspike has created a non-fungible token (NFT). These digital chits use clever cryptography to prove, without the need for a central authenticator, that a...
I recently read a book called The Age of AI. The book was intended to provide an overview of the approaching trends for artificial intelligence (AI). The purpose of this article is not meant to provid...
What is the general public’s impression of artificial intelligence (AI)? It isn’t always easy to gauge. AI-powered voice assistants like Siri and Alexa are in our phones, our homes and even our cars, ...
Artificial intelligence (AI) adoption is on the rise. According to a recent McKinsey survey, 55 per cent of companies use artificial intelligence in at least one function, and 27 per cent attribute at...
A new method automatically describes, in natural language, what the individual components of a neural network do. Neural networks are sometimes called black boxes because, despite the fact that they c...
Over the past decade a niche of fintech wealth management firms including Wealthfront, Personal Capital and Betterment tackled one of the biggest disruptive challenges: financial services. Wealthfront...
Cybersecurity teams are eager to deploy AI-powered tools and are driven by factors including persistent hiring challenges. Vendors are eager to sell their AI-powered tools either to differentiate thei...
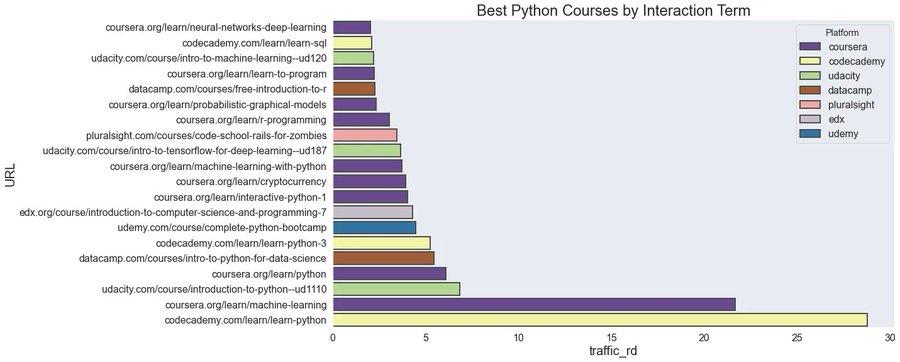
What does the data reveal if we ask: « What are the 10 Best Python Courses? ». Collecting almost all of the courses from top platforms shows there are plenty to choose from, with over 3000 offerings. ...
Machine learning tools are used in a variety of fields, from sales to medicine. But getting tech into the workplace is just one step — these tools are only successful if they’re integrated into workfl...
While business leaders grapple with the problem of cybercrime, they may be overlooking the giant cybercrime wave that quantum computing will bring. Quantum supremacy is the inflection point at which q...
Tesla’s Director of Artificial Intelligence, Andrej Karpathy, says that he believes ‘Tesla Bot’ is “on track to become the most powerful AI development platform.” Since Tesla AI Day last year, CEO Elo...
Precious metal investors have faced a grueling year as gold prices contracted after two years of gains. In recent days, however, gold and silver prices reached their highest levels since the sharp sel...
Russian President Vladimir Putin has called for consensus between his country’s government and the central bank following the latter’s recent call for an outright ban on crypto. Speaking i...
The debate over whether AI will replace humans in the workforce often boils down to a handy, twofold explanation: AI will replace humans for most repetitive and manual labor tasks, while humans will e...