When organizations accelerate their digital transformation due to the pandemic two years ago, many did not prioritize cybersecurity. In fact, organizations were focused mostly on ensuring business con...
With the number of digital-only ‘neobanks’ in the UK on the rise, the top four alone have over 12 million account holders between them, according to research by Insider Intelligence. As a rapidly expa...
AI-generated photos, also known as synthetic media, are being used to create fake experts and journalists to spread disinformation. Synthetic media is a broad, umbrella term that includes, among other...
For the past decade, artificial intelligence has been used to recognize faces, rate creditworthiness and predict the weather. At the same time, increasingly sophisticated hacks using stealthier method...
The FIDO Alliance is pushing for smartphones to become the authentication standard as the tech industry presses for new methods. The FIDO Alliance wants to use smartphones as a true mobile authenticat...
Extracting the value of artificial intelligence requires gaining quick wins while developing at enterprise scale. Consider focusing on these key AI areas It’s an exciting and scary time to be a techno...
Peter Ricketts’ warning comes as UAE accused of using Pegasus spyware to hack into mobile phone at Downing Street Boris Johnson should “pay close attention” to basic rules of cybersecurity, a former n...
Our first responders have used established wireless modes of communication to address emergencies for the past two decades. Robots are now joining the effort. As we continue to augment public safety a...
Two astronomers make the case that uncrewed missions are a superior option to putting humans in space. Everyone loves astronauts. Whether actual or fictional—Buzz Aldrin or Buzz Lightyear—astronauts e...
Artificial intelligence (AI) researcher Sandra Wachter says that although the House of Lords inquiry into police technology “was a great step in the right direction” and succeeded in highlighting the ...
Griffith previously pleaded guilty to one count of conspiracy to violate international sanctions for giving a talk at a crypto conference in Pyongyang in 2019. Former Ethereum developer Virgil Griffit...
Adecade ago security researcher Barnaby Jack famously wirelessly hacked a hospital insulin pump live on stage in front of hundreds of people to demonstrate how easily it could be compromised to delive...
Cyberattacks are more common, costly and consequential than ever. VMware Carbon Black found that up to 99% of U.K. companies have suffered data breaches in the past 12 months. Hiscox reported that a U...
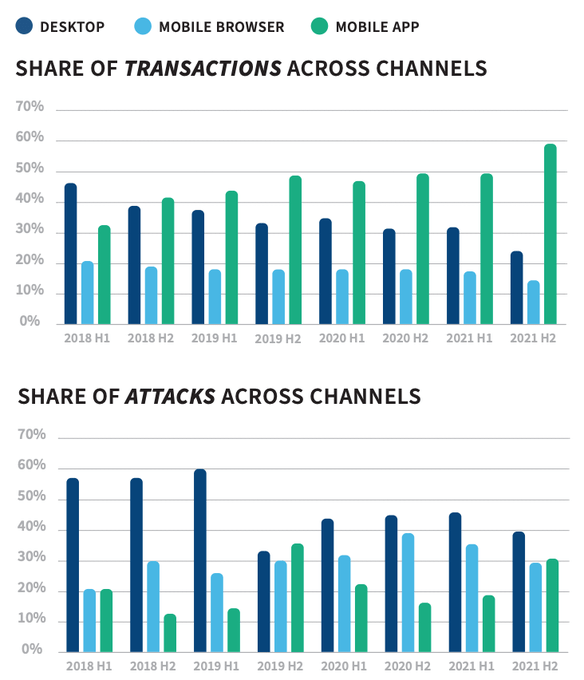
Fraud patterns are changing considerably as consumer dependence on the mobile channel continues to increase. Over the past three years, the share of attacks on mobile channels, versus desktop, has ris...
Encryption software protects confidential and private data in transit and at rest by making it accessible only to authorized individuals. Learn about the best encryption software and techniques. Encry...