Du 22 janvier au 9 février 2024, 4 000 lycéens et « près de 1 000 lycéennes » vont s’immerger dans le rôle de « hackers » en participant à la seconde édition du challenge « Passe ton hack d&rsqu...
Les vétérans de la prestigieuse unité de renseignement militaire israélienne sont recrutés par les entreprises de cybersurveillance les plus performantes du pays. Un quart des salariés du groupe NSO, ...
Le pentester effectue des tests d’intrusion pour vérifier la sécurité informatique de l’entreprise et fournit des solutions pour réduire sa vulnérabilité. Sa fonction est de contrôler la sécurité...
Multi-factor authentication (MFA) continues to embody both the best and worst of business IT security practice. As Roger Grimes wrote in this article about two-factor hacks three years ago, when MFA i...
September 17, 2020 Chinese Nationals Charged With Hacking Attacks “The United States government is starting to turn the tide on Chinese intrusion operations on Western companies and targets. » U.S. au...
A viral article in the Russian newspaper Kommersant claimed that a user on a Russian hacker forum had acquired the personal information of 7.6 million voters in Michigan and other voters in several ot...
Spécialisé dans la diffusion illégale de films et séries, souvent avant même leur sortie officielle, le groupe Sparks a vu deux de ses membres arrêtés. Source : Piratage : deux membres du groupe Spark...
Apple Security Research Device Program As part of Apple’s commitment to security, this program is designed to help improve security for all iOS users, bring more researchers to iPhone, and improve eff...
A new cryptojacking botnet is spreading across compromised networks via multiple methods that include the EternalBlue exploit for Windows Server Message Block (SMB) communication protocol. Researchers...
Welcome to the Network Ethical Hacking course! Hacking is a science similar to any other science. In this course I am going to show you the basics of hacking which will support you to start by yoursel...
The more we depend on smartphones, the more attractive an attack vector they become. Android and iOS and devices have become common targets for cybercriminals, as people use them for work, communicati...
Morocco Asks Amnesty for Proof It Used Spyware on Journalist Morocco’s prime minister has demanded Amnesty International provide evidence to support its allegations that Rabat used spyware to bu...
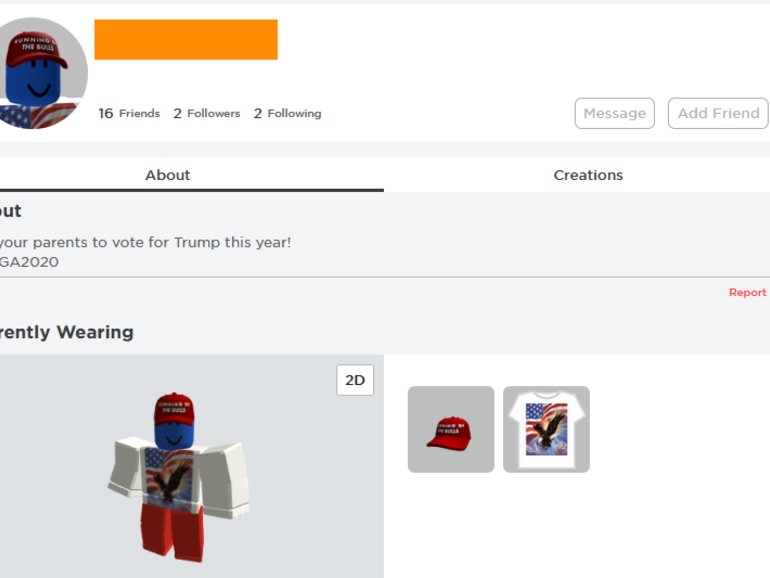
Hackers are taking Roblox credentials leaked on Pastebin, accessing accounts, and leaving the same « Ask your parents to vote for Trump this year » message on thousands of Roblox profiles. Hackers hav...
A top-secret communications system used by criminals to trade drugs and guns has been « successfully penetrated », says the National Crime Agency. The NCA worked with forces across Europe on the UK&rs...
The authority will now review and request additional information from holders in the 10 locked-down postcodes after a surge of licence amendments were lodged as people tried desperately to avoid stage...