Here are the five best HackerNoon articles related to artificial intelligence in February. I hope they will help you learn more about machine learning this year. Note that the five articles you...
Why are interest rates on dollar-pegged stablecoins so much higher than interest rates on actual dollars? You’d think that a stablecoin worth a dollar would command the same interest rate as a dollar,...
If job seekers knew companies were using artificial intelligence to fill open positions, would it stop them from applying for the job? The answer, according to a recent study, is yes—sometimes. The re...
War Has Again Arrived In Europe Day ten of the war and it appears that a called for ceasefire to allow civilians a corridor for escape from the Russian bombardment of Ukraine’s urban centers has faile...
If blockchain technology is to reach true mass adoption, it will have to become cheaper and more efficient. Low transaction throughput on some of the most popular blockchains, most notably Ethereum, h...
Age-old biases are being hard-wired into new age tech in predictive and profiling AI systems Indian police have also moved to using AI-based technology in efforts to control crimes On 1 March, more th...
Par-delà les cyberattaques de désinformation, il est évident que la gouvernance russe ne va pas rester inactive sur le terrain de la contre-offensive liée aux sanctions qui la menacent. Nonobstant les...
You are not the only one who think that Artificial intelligence is something to watch over. Up to now, one thing remains clear: whatever the future holds, AI will most definitely play an important rol...
The service bot will revolutionize warehouses, hospitals, farms, and maybe your home. There are now some 120,000 warehouses globally, and another 50,000 are likely to be added before 2025. Over the ne...
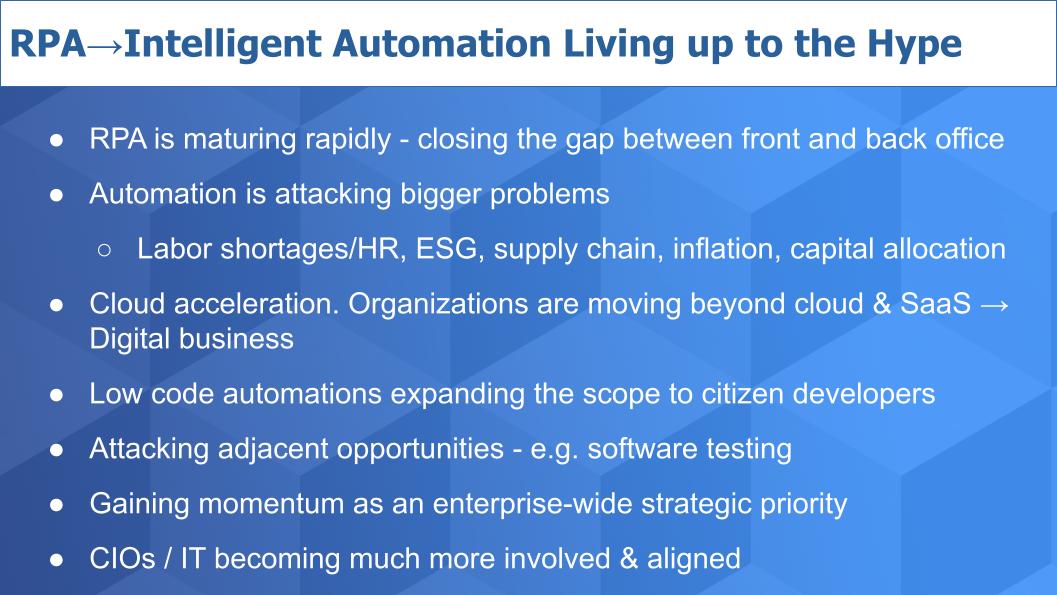
In its early days, robotic process automation emerged from rudimentary screen scraping, macros and workflow automation software. Once a script-heavy and limited tool that was almost exclusively used t...
It took me a long process of reflection and self-adjustment to transcend all that. In this article, I detail the course of my first five years of experience, which started with grotesque innocence and...
In recent years, scientists have been working on a variety of systems that can identify and traverse items in their environment. Most of these systems rely on deep learning and machine learning algori...
Elon Musk shared some interesting tweets about Tesla’s AI this weekend, and even a cool idea that would bring innovation to those old traffic lights that take forever to change at 2:00 am even though ...
Databases are fundamental to training all sorts of machine learning and artificial intelligence (AI) models. Over the last two decades, there has been an explosion of datasets available on the market,...
The average business receives 10,000 alerts every day from the various software tools it uses to monitor for intruders, malware, and other threats. Cybersecurity staff often find themselves inundated ...