FOR GENERATIONS, THE inhabitants of the Arctic have counted on seasonal sea ice, which grows and retreats during the year. Polar bears and marine mammals rely on it as a hunting spot and a place to re...
US activist raises concerns over racial bias in AI Urges software developers to listen more to Black people Wrongful arrest in US caused by faulty facial recognition Lisbon playing host to Europe&rsqu...
The man responsible for ensuring the EU’s institutions stick to its data protection laws believes Europe isn’t ready for facial recognition tech that watches people in public. European “so...
It’s the AI system once deemed too dangerous to release to the public by its creators. Now, Microsoft is making an upgraded version of the program, OpenAI’s autocomplete software GPT-3, available to b...
The World Economic Forum’s The Future of Jobs Report 2020 estimates that 85 million jobs could be “displaced” by AI before 2025. Whether you treat the technology with suspicion or embrace it wholehear...
A firm which claims to have a database of more than 10 billion facial images has breached Australia’s privacy laws, Australian regulators say. Clearview AI lets law enforcement agencies search i...
Delphi, an online AI bot, promises to answer any moral question users pose. We put it to the test Corporal punishment, wearing fur, pineapple on pizza – moral dilemmas, are by their very nature, hard ...
The world of business changed so much in the last year. When companies sent employees to work from home at the start of the Covid-19 pandemic it sparked massive growth in digital footprints. That grow...
AI is often viewed as the death of creativity. Yet, as Maximilian Niemann, a director at Unit9 production company, points out, when machines are used in collaboration with humans, it may actually make...
How would an AI writing program start an article on the future of AI writing? Well, there’s one easy way to find out: I used the best known of these tools, OpenAI’s GPT-3, to do the job for me. Using ...
The future could see the world’s human data, delivered through the rising power and reach of artificial intelligence, in the hands of a powerful few – a recipe for a dystopian tomorrow pop...
People tend to rejoice in the disclosure of a secret. Or, at the very least, media outlets have come to realize that news of “mysteries solved” and “hidden treasures revealed” generate traffic and cli...
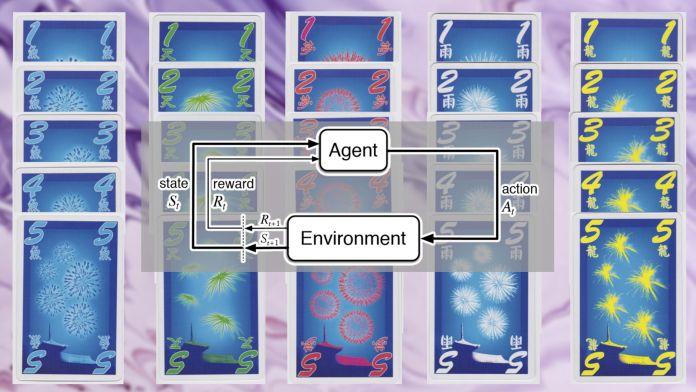
Artificial intelligence has proven that complicated board and video games are no longer the exclusive domain of the human mind. From chess to Go to StarCraft, AI systems that use reinforcement learnin...
Artificial intelligence, or AI, has been a buzzword for a while now. Although it has its own set of rewards and accolades mustered through disciplines like machine learning (ML), deep learning (DL) an...
La société GitHub a annoncé que son assistant de codage est désormais capable d’écrire 30% des codes hébergés sur sa plateforme. GitHub a annoncé que son assistant de programmation, GitHub Copilot, es...