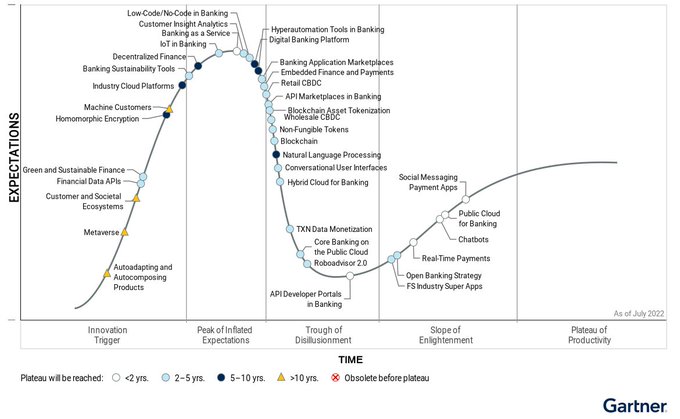
Banking-as-a-Service (BaaS) will hit mainstream adoption within two years, according to the latest Gartner Hype Cycle for Digital Banking Transformation. Gartner predicts that 30% of banks with greate...
For years, anyone seeking a role model for successful businesses could look to the world of tech and fintech. Companies such as “buy now, pay later” pioneer Klarna — once Europe’s most valuable privat...
Forbes’ Diane Brady sits down with EndeavorVR CEO Amy Peck to talk about all things metaverse, including the current investment landscape, pain points, and who is doing it well. 0:00 Introducing Amy P...
Banking involvement in the metaverse will enable exponential growth of the ‘creative economy.’ In order to prepare for the impending metaverse acceleration, financial institutions must acq...
JPMorgan Chase has agreed to acquire a payments startup called Renovite to fend off threats from fintech firms including Stripe and Block, CNBC has learned. While JPMorgan is often content to partner ...
Les attaques de rançongiciels ciblant Linux sont en forte hausse, les cybercriminels cherchant à élargir leurs options et à cibler un système d’exploitation souvent négligé par les entreprises e...
De l’analyse de la situation à la réparation de vos défenses en passant par les secours à appeler, voici la marche à suivre si vous êtes la cible de cybercriminels. Vendredi soir, vous êtes sur ...
La guerre en Ukraine se mue en guerre monétaire. La Chine vient d’annoncer qu’elle payera le gaz russe en yuan tandis que l’Iran vient de légaliser le paiement d’importations en bitcoin. Le géant russ...
Ten years ago, I co-wrote and sold a comedy film script to 20th Century Fox. Called “The Lose,” the elevator pitch was “The Fugitive meets Harold & Kumar set in Southeast Asia.” Fox ended up shelv...
Why has machine learning become so vital in cybersecurity? This article answers that and explores several challenges that are inherent when applying machine learning. Machine learning (ML) is a common...
On a Sunday afternoon, I was going through chat transcripts produced by our chatbot, which sits on our company’s website, greeting visitors and answering their questions. One transcript caught my eye ...
6 AI startups and the pitch decks they used to raise funding from investors like Goldman Sachs, Tiger Global, and Microsoft’s M12 Artificial-intelligence, machine-learning, and data-analysis AI ...
Damien Hirst cut a cow and calf each lengthwise into two halves and displayed them in four separate baths of formaldehyde in clear display tanks. The title of the creation, “Mother and Child Divided,”...
An artificial intelligence can decode words and sentences from brain activity with surprising — but still limited — accuracy. Using only a few seconds of brain activity data, the AI guesses what a per...
Businesses across industries are increasingly using artificial intelligence in a variety of ways to improve their internal operations, from handling repetitive tasks to interpreting data to streamlini...