Ten years ago, I co-wrote and sold a comedy film script to 20th Century Fox. Called “The Lose,” the elevator pitch was “The Fugitive meets Harold & Kumar set in Southeast Asia.” Fox ended up shelv...
Why has machine learning become so vital in cybersecurity? This article answers that and explores several challenges that are inherent when applying machine learning. Machine learning (ML) is a common...
An AI trained to assess heart scans outperformed human technicians, both in terms of accuracy and efficiency, in a first-of-its-kind trial. “There’s a lot of hype and a lot of excitement around AI, bu...
Los Angeles Unified, with over 600,000 students, suffers ‘significant infrastructure disruption’ but classes set to take place as usual Hackers targeted the second-largest school district in the US wi...
This year marks the 25th anniversary of the cyber insurance market. While many industry observers view cyber coverage as a surging phenomenon in response to escalating incidence of random attacks, the...
Modern cyber attackers’ tactics, techniques, and procedures (TTPs) have become both rapid and abundant while advanced threats such as ransomware, cryptojacking, phishing, and software supply chain att...
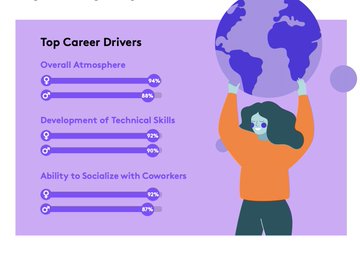
Logitech MX and Girls Who Code surveyed 400 Tech and IT workers, revealing the most influential breakthrough factors for women pursuing careers in these industries. By educating about these key barrie...
From the Mayor’s Office to France’s first tech incubator for female leaders, Caroline Ramade has dedicated her career to tackling tech’s huge issue of female retention. Gender balanc...
Patrick Hillmann, chief communications officer at the world’s largest crypto exchange, Binance, claims scammers made a deepfake of him to trick contacts into taking meetings. Writing in a blog post ti...
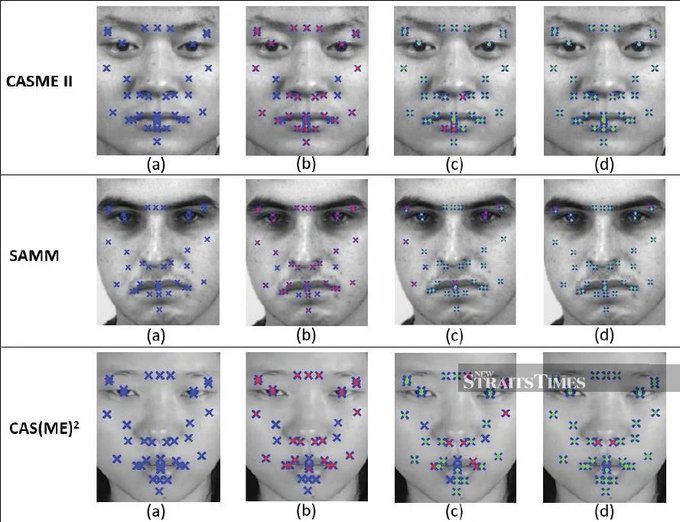
UNIVERSITY PARK, Pa. — Mobile devices use facial recognition technology to help users quickly and securely unlock their phones, make a financial transaction or access medical records. But facial recog...
Consider the following cybersecurity breaches – all from within the past three months: GitHub, the leading cloud-based source control service, discovered that hackers capitalized on stolen OAuth token...
The world is getting more and more digitized with each passing day, especially with the augmentation of hybrid working spaces. Millions of lines of data are being processed and stored online with an i...
Here are the top habits of successful data and AI-driven organizations We’re currently in a “data renaissance” where enterprises realize that to execute on novel data and AI use cases, the legacy mode...
ARTIFICIAL intelligence (AI) has dramatically altered our lifestyle for the better, be it at work, school or play. But as AI gets ‘menial’ tasks done with ridiculous ease, bad actors see i...
Un détournement de mineurs en cours ? – L’approche du fameux « The Merge » sur Ethereum continue d’alimenter les discussions de passionnés. Entre les mineurs, les développeurs, les fans et les observa...