A major new report on the state of artificial intelligence (AI) has just been released. Think of it as the AI equivalent of an Intergovernmental Panel on Climate Change report, in that it identifies w...
The best AI projects are the ones where people aren’t afraid of messing things up or wasting valuable time reinventing processes. Even if you’re not familiar with artificial intelligence (...
Cloud services provide resources on a massive scale to support artificial intelligence and machine learning efforts, but a hybrid approach may be the best course in many cases. That requires an enterp...
Some problems are so big, you can’t really see them. Climate change is the perfect example. The basics are simple: the climate is heating up due to fossil fuel use. But the nitty gritty is so va...
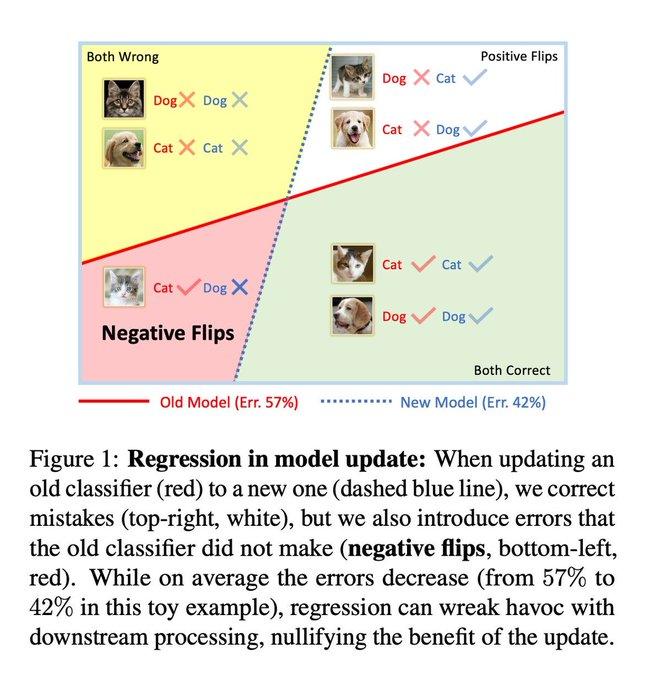
In what’s called « Graceful AI, » Amazon AWS AI lead Stefano Soatto and colleagues work to solve industrial problems that in turn may produce new insights into the fundamentals of deep learning ...
A book review of “The Age of AI” written by Henry A Kissinger, Eric Schmidt, and Daniel Huttenlocher An AI learned to win chess by making moves human grandmasters had never conceived. Another AI disco...
A major new report on the state of artificial intelligence (AI) identified where AI is at today, and the promise and perils in view. AI has begun to permeate every aspect of our lives, from language g...
This is part 2 of Natalie’s Permission to Be Uncertain series. The interviews in this series explore how today’s AI practitioners, entrepreneurs, policy makers, and industry leaders are thinking about...
Artificial Intelligence (AI) sometimes gets a really bad reputation for taking over Earth in the future! 🤖 If you’ve watched, The Terminator, then you may even have even stronger feelings about this! ...
Apple has taken a public stand on privacy, curtailing data abuses by apps and declaring it doesn’t exploit its users’ information. But it has also created comprehensive new ways to track us Among tech...
Microsoft says that Russian-sponsored hacking groups are increasingly targeting US government agencies, with roughly 58% of all nation-state attacks observed by Microsoft between July 2020 and June 20...
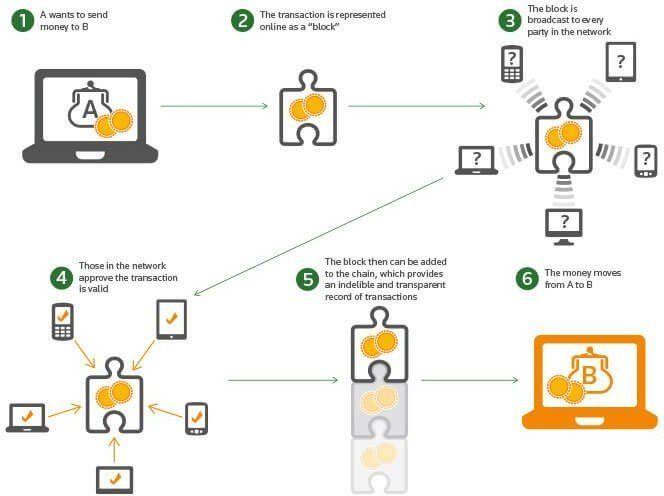
Combining big data and blockchain is valuable for supply chain, financial services, healthcare and insurtech organizations by providing them better data storage, integrity, accessibility and security....
Artificial intelligence is often thought of as disembodied: a mind like a program, floating in a digital void. But human minds are deeply intertwined with our bodies — and an experiment with virtual c...
Google has recently announced the launch of Google Cloud Skills Boost, a platform for online learning, skills development, and certifications, managed and delivered directly by Google Cloud. Google sa...
Long viewed as a relative laggard, Japan’s start-up ecosystem is beginning to come into its own. Investor Paul McInerney sheds light on the evolving environment for entrepreneurs. In this episode of t...