McAfee Entreprise publie son rapport sur les menaces avancées (Octobre 2021), qui examine l’activité cybercriminelle liée aux ransomwares et aux menaces liées au cloud au cours du deuxième trimestre 2...
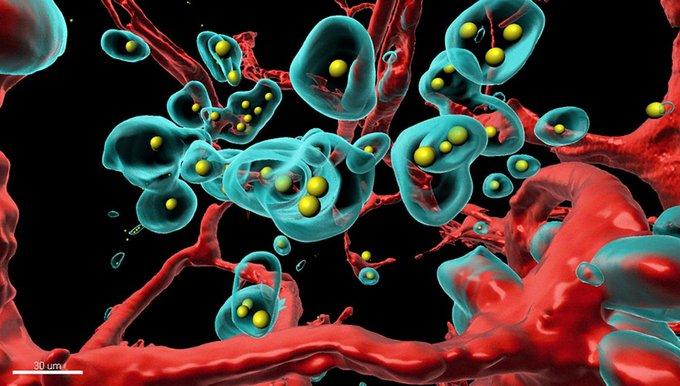
A new technology developed by UZH researchers enables the body to produce therapeutic agents on demand at the exact location where they are needed. The innovation could reduce the side effects of canc...
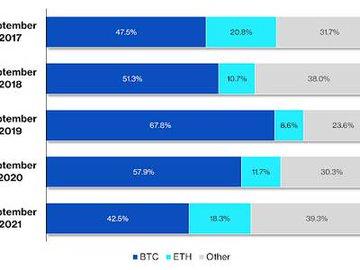
The original blockchain still reigns, but neither Bitcoin nor its closest competitor, Ethereum, can count on becoming the only game in town any time soon. On Tuesday, CoinDesk Research will drop its Q...
In 2015 a cohort of well-known scientists and entrepreneurs including Stephen Hawking, Elon Musk, and Steve Wozniak issued a public letter urging technologists developing artificial intelligence syste...
We’ve all seen movies where AI takes over the world (I, Robot is probably my favorite) but what are the potential harms of it in the current day. Let’s try and understand from where can these dangers ...
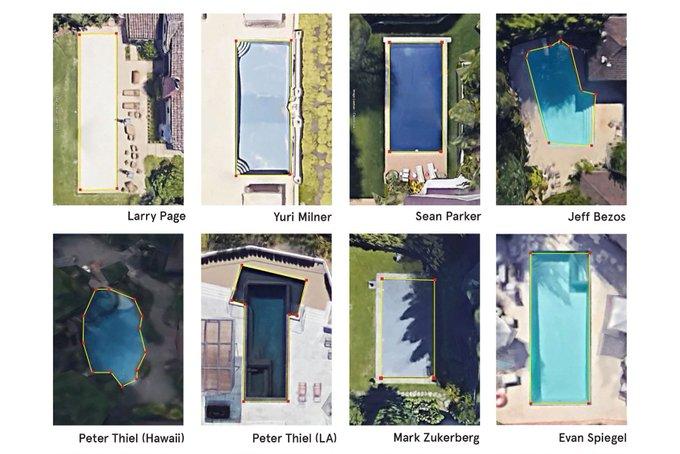
When it comes to digital transformation, the Covid crisis has provided important lessons for business leaders. Among the most compelling lessons is the potential data analytics and artificial intellig...
Millions of pounds were swiped from Barclays accounts in a series of coordinated cyberattacks by a fraudster using a Monzo account and a payments initiation service provider (PISP), The Telegraph repo...
The emergence of data science as a field of study and practical application over the last century has led to the development of technologies such as deep learning, natural language processing, and com...
Interview : en quoi un ordinateur quantique est-il différent ? Le monde quantique est fascinant : à cette échelle, par exemple, les objets peuvent se trouver simultanément dans plusieurs états. Expl...
Some languages that have never been deciphered could be the next ones to get the machine translation treatment. In 1886, the British archaeologist Arthur Evans came across an ancient stone bearing a c...
Threat actors are trying to capitalize on the recent revelations on Pegasus spyware from Amnesty International to drop a less-known remote access tool called Sarwent. The malware looks and acts the pa...
Un chercheur a trouvé un moyen d’insérer du code malveillant en lieu et place du numéro de contact que cet accessoire peut diffuser à celui qui le trouve. Version high-tech du porte-clés siffleur, l’A...
La protection des données personnelles n’est visiblement pas la priorité de la police judiciaire. À l’issue de contrôles effectués en 2019, la CNIL a constaté une série de manquements concernant le tr...
Des centaines d’applications vérolées sur Google Play souscrivaient des services SMS Premium pour 30 euros par mois. Un nouveau cheval de Troie se diffuse massivement auprès des utilisateurs Android. ...
We’ve searched the Thinkers360 Content Library to pick out 50 podcasts on business and technology from Thinkers360 member thought leaders. Here’s our picks (listed in alphabetical order) with direct l...