Veille cyber Highest ranked #insurtech content from the past 7 Days The algorithm reads every tweet and filters out links to stuff it has seen before: ignoring retweets, duplicate posts, shortened URL...
L’audience provenant de Google reste LA source de trafic n°1 en matière de leviers digitaux. A titre d’exemple, le SEO représente un peu plus de 60% de notre audience. Le SEO, en plus d’apporter du tr...
Une mise à jour de Google Chrome est disponible et doit être installée rapidement : elle corrige plusieurs vulnérabilités, dont deux sont exploitées. Internautes qui utilisez Google Chrome pour aller ...
Aujourd’hui, de nombreux outils SEO sont à la disposition des entreprises pour l’optimisation du référencement de leur site. Outils de suivi de position, d’analyse de backlinks, d’audit de site, outil...
L’ascension de la cryptomonnaie a vu naitre escroqueries et arnaques en tout genre. Nouveaux comme anciens utilisateurs peuvent tous tomber dans les pièges. D’ailleurs, les pirates informatiques ne so...
Getting the software right is important when developing machine learning models, such as recommendation or classification systems. But at eBay, optimizing the software to run on a particular piece of ...
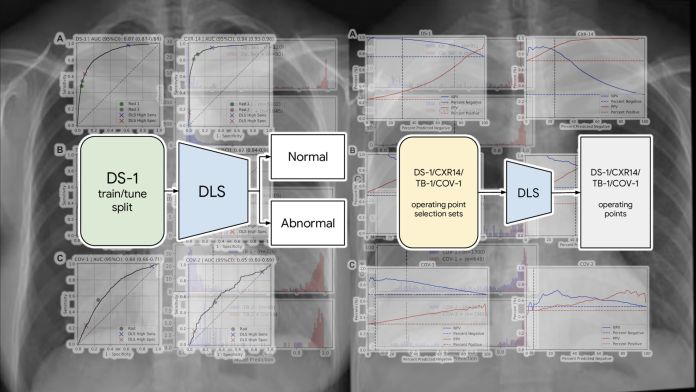
This article is part of our reviews of AI research papers, a series of posts that explore the latest findings in artificial intelligence. Deep learning can detect abnormal chest x-rays with accuracy t...
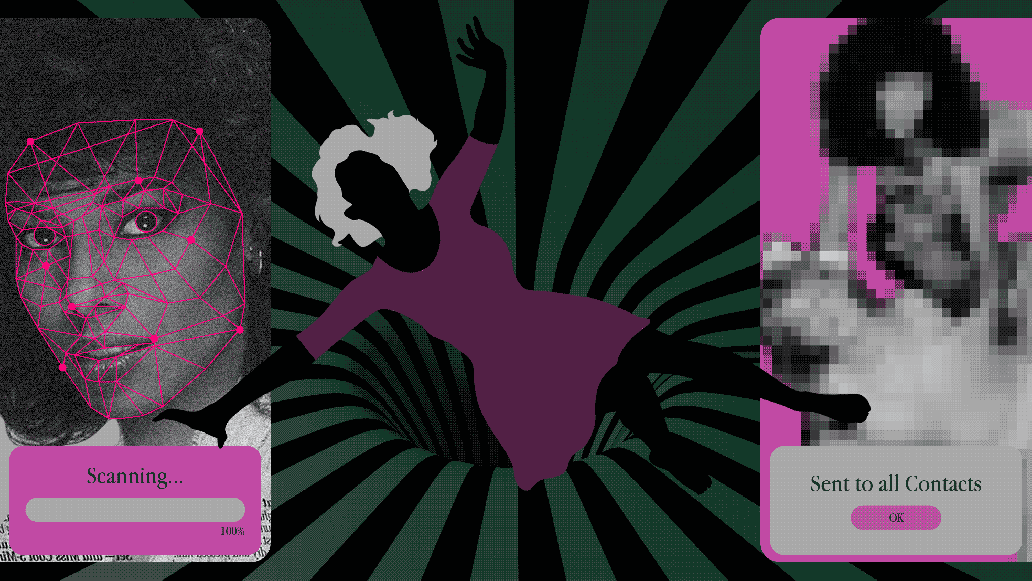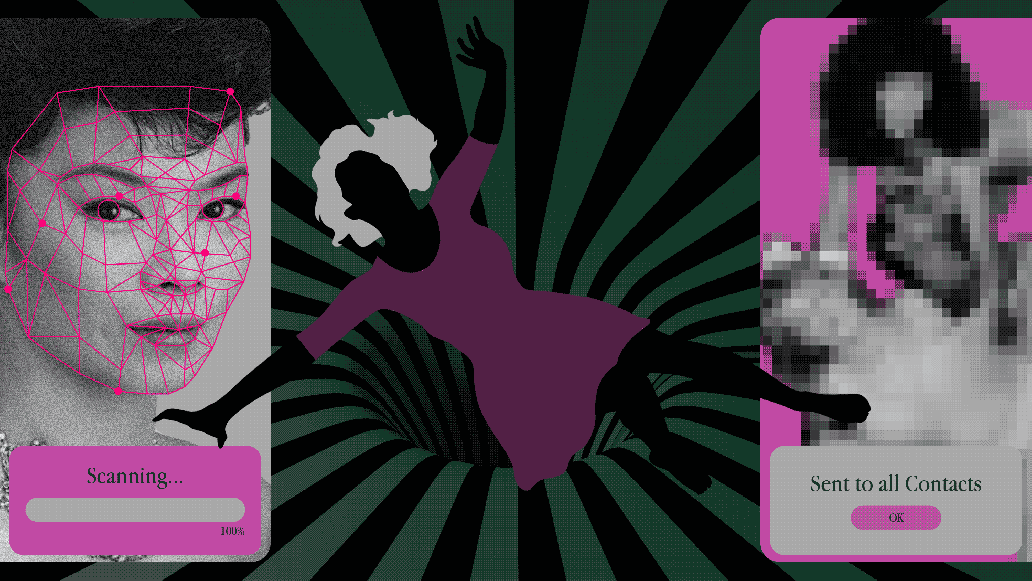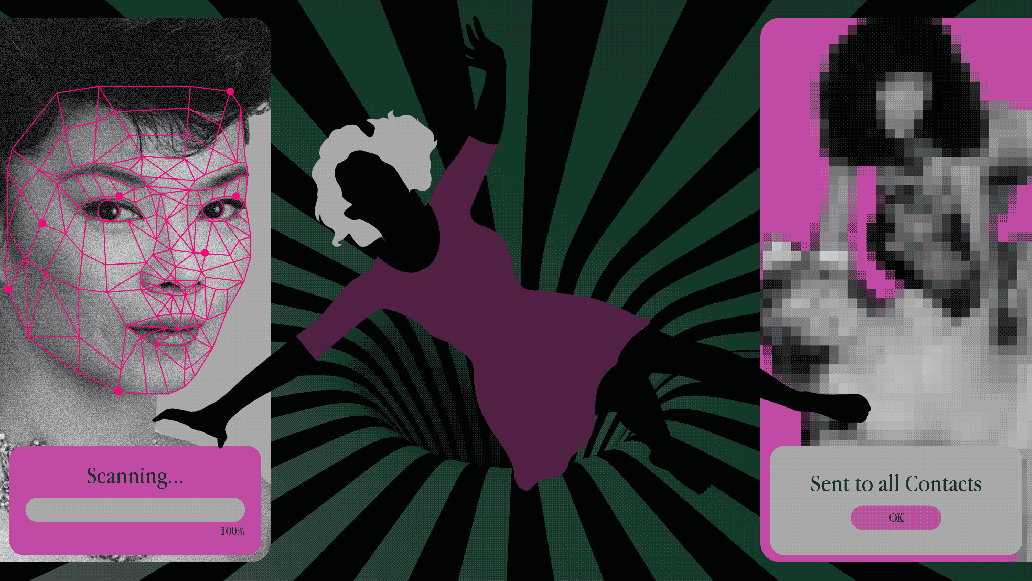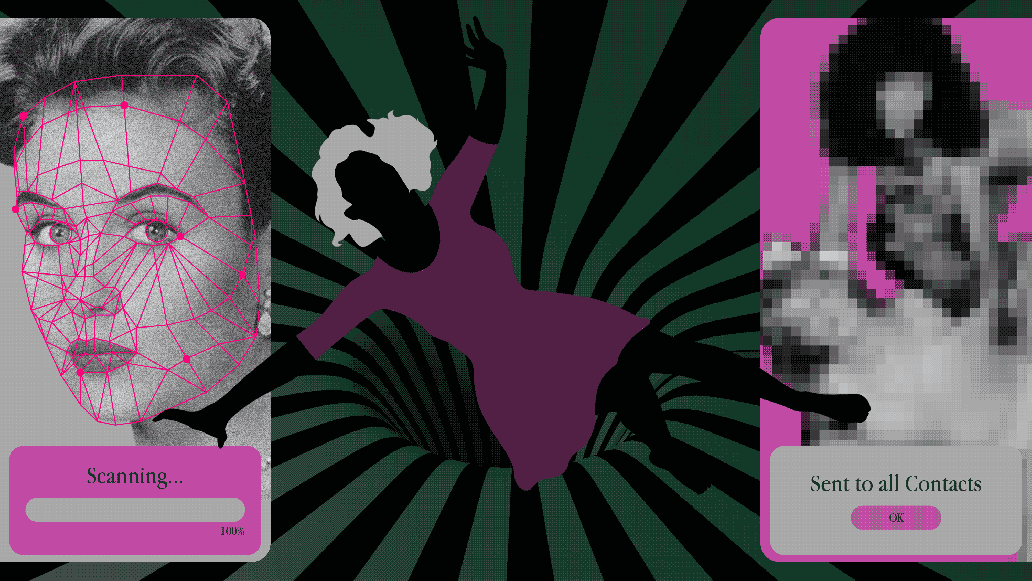
The website is eye-catching for its simplicity. Against a white backdrop, a giant blue button invites visitors to upload a picture of a face. Below the button, four AI-generated faces allow you to tes...
For years, curators have attempted to use the latest technology to help modern audiences connect with centuries-old art — and the paintings of Dutch artist Rembrandt van Rijn are at the forefront. Som...
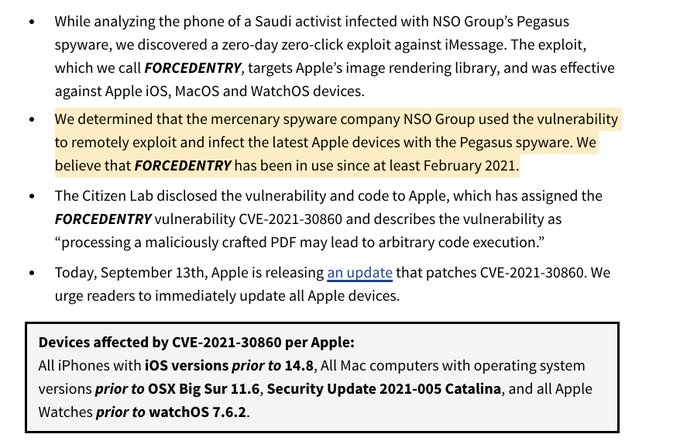
Summary While analyzing the phone of a Saudi activist infected with NSO Group’s Pegasus spyware, we discovered a zero-day zero-click exploit against iMessage. The exploit, which we call FORCEDENTRY, t...
As part of the Biden administration’s wide-ranging cybersecurity executive order (EO) issued in May, the Office of Management and Budget (OMB) and the Cybersecurity and Infrastructure Security A...
The cybersecurity world’s favorite catchphrase isn’t any one product or system, but a holistic approach to minimizing damage. FOR YEARS A concept known as “zero trust” has been a go-to cybersecurity c...
À la suite de la distribution de plusieurs centaines de passes sanitaires frauduleux, une enquête a été confiée à la police judiciaire du chef «d’intrusion illicite dans un système de traitement...
A Beginner’s Guide To The Internet Of Things (IoT) 2021 We are able to turn on the lights in our homes from a desk in an office miles away. The built-in cameras and sensors embedded in our refri...
Most of the public discourse around artificial intelligence (AI) policy focuses on one of two perspectives: how the government can support AI innovation, and how the government can deter its harmful o...